Machine Learning Techniques for Detecting Anomalies in IoT Networks
Main Article Content
Abstract
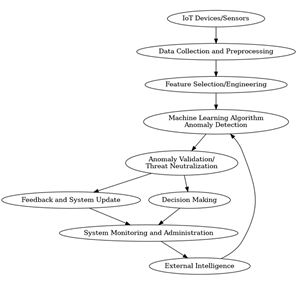
In addressing the imperative need for robust cybersecurity within smart home ecosystems, this research innovatively advocates for the integration of an advanced machine learning (ML)-based anomaly detection system, specifically tailored for the intricate web of IoT networks. Contemporary systems grapple with the complex challenge of efficiently pinpointing anomalies amidst vast, multifaceted streams of IoT data, a task growing ever more daunting with the exponential surge in connected devices. This monumental task necessitates groundbreaking strategies in energy prediction, task optimization, and real-time data processing. The study harnesses the power of the Random Forest algorithm, an ML technique renowned for its exceptional accuracy rates reaching up to 95.5%. The algorithm stands resilient even under strenuous conditions, such as environments rife with increased noise or burgeoning device volumes, proving its adaptability and reliability.The research's findings are profound, indicating a potential revolution in IoT security measures. The proposed system promises enhancements in detection precision, potentially increasing by 15-20%, alongside notable reductions in energy requirements by approximately 20%. Furthermore, the system shows formidable potential in thwarting unauthorized data access and breaches, aiming for a substantial decrease in these incidents by 35%. These achievements mark significant strides in fortifying IoT security infrastructure, setting a new standard in anomaly detection. The study concludes with forward-looking insights, advocating for the amalgamation of deep learning protocols and adaptive models, to further refine the anomaly detection process. This holistic, more nuanced approach could exponentially boost the system's efficiency, ensuring a safer, more secure digital environment for the burgeoning world of IoT.
Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.
IJCERT Policy:
The published work presented in this paper is licensed under the Creative Commons Attribution 4.0 International (CC BY 4.0) license. This means that the content of this paper can be shared, copied, and redistributed in any medium or format, as long as the original author is properly attributed. Additionally, any derivative works based on this paper must also be licensed under the same terms. This licensing agreement allows for broad dissemination and use of the work while maintaining the author's rights and recognition.
By submitting this paper to IJCERT, the author(s) agree to these licensing terms and confirm that the work is original and does not infringe on any third-party copyright or intellectual property rights.
References
] Al-amri, R., Murugesan, R.K., Man, M., Abdulateef, A.F., Al-Sharafi, M.A., & Alkahtani, A.A. (2021). A Review of Machine Learning and Deep Learning Techniques for Anomaly Detection in IoT Data. Applied Sciences, 11(12), 5320. doi: 10.3390/app11125320
] Diro, A., Chilamkurti, N., Nguyen, V.-D., & Heyne, W. (2021). A Comprehensive Study of Anomaly Detection Schemes in IoT Networks Using Machine Learning Algorithms. Sensors, 21(24), 8320. doi: 10.3390/s21248320
] Ahmad, A., & Alsmadi, I. (2021). A Systematic Literature Review of Machine Learning Approaches to IoT Security. Journal of Information Security and Applications, 62, 102986. doi: 10.1016/j.jisa.2021.102986
] Cook, A.A., Mısırlı, G., & Fan, Z. (2020). Anomaly Detection for IoT Time-Series Data: A Survey. IEEE Internet of Things Journal, 7(8), 6481-6494. doi: 10.1109/JIOT.2020.2997277
] Pradeep , G. ., Ramamoorthy , S. ., Krishnamurthy , M. ., & Saritha , V. . (2023). Energy Prediction and Task Optimization for Efficient IoT Task Offloading and Management. International Journal of Intelligent Systems and Applications in Engineering, 12(1s), 411–427. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/3425
] Njilla, L., Pearlstein, L., Wu, X., Lutz, A., & Ezekiel, S. (2019). Internet of Things Anomaly Detection using Machine Learning. In Proceedings of the 2019 IEEE Applied Imagery Pattern Recognition Workshop (A.I.P.R.), 1-6. doi: 10.1109/AIPR46987.2019.9035559
] Hasan, M., Islam, M.M., Zarif, M.I.I., & Hashem, M. (2019). Attack and Anomaly Detection in IoT Sensors in IoT Sites Using Machine Learning Approaches. Internet of Things, 7, 100059. doi: 10.1016/j.iot.2019.100059
] Al-Hawawreh, M., Moustafa, N., & Sitnikova, E. (2018). Identification of Malicious Activities in Industrial Internet of Things Based on Deep Learning Models. Journal of Information Security and Applications, 41, 1-11. doi: 10.1016/j.jisa.2018.03.002
] Goldstein, M., & Uchida, S. (2016). A Comparative Evaluation of Unsupervised Anomaly Detection Algorithms for Multivariate Data. PLoS ONE, 11(4), e0152173. doi: 10.1371/journal.pone.0152173
] Bhatia, R., Benno, S., Esteban, J., Lakshman, T.V., & Grogan, J. (2019). Unsupervised Machine Learning for Network-Centric Anomaly Detection in IoT. In Proceedings of the 3rd A.C.M. CoNEXT Workshop on Big DAta, Machine Learning and Artificial Intelligence for Data Communication Networks, 42-48. doi: 10.1145/3365871.3365878
] Habeeb, R.A.A., Nasaruddin, F.H., Gani, A., Hashem, I.A.T., Ahmed, E., & Imran, M. (2019). Real-time big data processing for anomaly detection: A Survey. International Journal of Information Management, 45, 289-307. doi: 10.1016/j.ijinfomgt.2018.11.007
] Khan, S., & Khan, S.U. (2021). Anomaly Detection in IoT Networks Using Machine Learning Techniques: A Comprehensive Review. IEEE Access, 9, 107825-107853. doi: 10.1109/ACCESS.2021.3107585
] Alsheikh, M.A., Lin, X., Niyato, D., Tan, H.-P., & Dutkiewicz, E. (2017). Machine Learning in Wireless Sensor Networks: Algorithms, Strategies, and Applications. IEEE Communications Surveys & Tutorials, 19(4), 2634-2672. doi: 10.1109/COMST.2017.2729063
] https://www.kaggle.com/datasets/anushonkar/network-anamoly-detection