Enhancing Privacy in Social Media Photo Sharing: A User-Centric Framework Integrating Multi-Party Consent and Blockchain Technologies
Main Article Content
Abstract
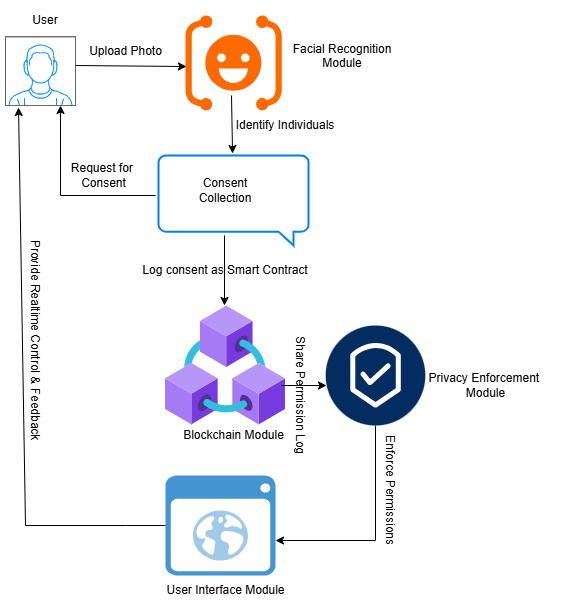
The widespread sharing of photographs on social networks has redefined digital communication, thereby raising privacy concerns related to control over visual data. Unlike textual content, photos involve multiple stakeholders, which complicates ownership and consent. This research addresses these challenges by proposing a Privacy Control Model that incorporates multi-party consent mechanisms, blockchain-based permission tracking, and user-centric design to enhance privacy management in photo sharing. Using the Facebook Social Network Dataset (SNAP), the model was evaluated across three key metrics: unauthorized viewing probability tagging) conflict rate) and user satisfaction ( . The results demonstrated a 70-79% reduction in unauthorized views, with decreasing from 38% (DPSM) to 8%. Tagging conflicts were reduced by 52-75%, with dropping from 48% (DPSM) to 12%. User satisfaction increased significantly from 2.9/5 (DPSM) to 4.7/5, reflecting the effectiveness of the model’s intuitive tools and transparency features. While the model proves robust, limitations include potential scalability issues owing to the computational requirements of facial recognition and blockchain, as well as dependence on user compliance and algorithm accuracy. Future work will address these concerns and explore broader applications for other media types, such as videos and live streams. This study underscores the potential of technology-driven, user-centric solutions to balance privacy and connectivity in photo sharing, paving the way for enhanced digital trust and user autonomy on social networks.
Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.
IJCERT Policy:
The published work presented in this paper is licensed under the Creative Commons Attribution 4.0 International (CC BY 4.0) license. This means that the content of this paper can be shared, copied, and redistributed in any medium or format, as long as the original author is properly attributed. Additionally, any derivative works based on this paper must also be licensed under the same terms. This licensing agreement allows for broad dissemination and use of the work while maintaining the author's rights and recognition.
By submitting this paper to IJCERT, the author(s) agree to these licensing terms and confirm that the work is original and does not infringe on any third-party copyright or intellectual property rights.
References
D. Boyd and N. B. Ellison, "Social network sites: Definition, history, and scholarship," Journal of Computer‐Mediated Communication, vol. 13, no. 1, pp. 210–230, 2007.
A. Acquisti, L. Brandimarte, and G. Loewenstein, "Privacy and human behavior in the age of information," Science, vol. 347, no. 6221, pp. 509–514, Jan. 2015.
A. M. Kaplan and M. Haenlein, "Users of the world, unite! The challenges and opportunities of Social Media," Business Horizons, vol. 53, no. 1, pp. 59–68, Jan. 2010.
J. Tang, J. Zhang, X. Wang, and H. Liu, "A survey of social media analytics: Research applications, opportunities, and directions," IEEE Transactions on Knowledge and Data Engineering, vol. 29, no. 12, pp. 2764–2783, Dec. 2017.
M. S. Rahman, P. P. Mitra, and N. S. Khan, "Privacy concerns and privacy protection in social networks: A review," IEEE Access, vol. 8, pp. 183437–183470, Sep. 2020.
S. Zuboff, The Age of Surveillance Capitalism: The Fight for a Human Future at the New Frontier of Power, New York, NY, USA: PublicAffairs, 2019.
A. T. Campbell et al., "From smart to cognitive: The era of networked intelligence," IEEE Internet Computing, vol. 17, no. 4, pp. 4–7, Jul. 2013.
A. Westin, Privacy and Freedom, New York, NY, USA: Atheneum, 1967.
D. Boyd and A. Marwick, "Social privacy in networked publics: Teens’ attitudes, practices, and strategies," in A Decade in Internet Time: Symposium on the Dynamics of the Internet and Society, Oxford, UK, 2011.
J. Zimmermann and J. B. Young, "Social media privacy: Understanding user concerns for sharing photos," International Journal of Human-Computer Studies, vol. 134, pp. 102–112, Sep. 2020.
S. Baruh, C. Secinti, and Z. Cemalcilar, "Online privacy concerns and privacy management: A meta-analytical review," Journal of Communication, vol. 67, no. 1, pp. 26–53, Feb. 2017.
P. Kumar and E. Carbone, "Social media privacy settings: Who uses them and how?" Computers in Human Behavior, vol. 74, pp. 45–52, Sep. 2017.
M. S. Rahman, P. P. Mitra, and N. S. Khan, "Privacy concerns and privacy protection in social networks: A review," IEEE Access, vol. 8, pp. 183437–183470, Sep. 2020.
N. Christin, "Privacy in the digital age: Research challenges and emerging solutions," Communications of the ACM, vol. 61, no. 11, pp. 56–66, Nov. 2018.
J. Leskovec and A. Krevl, "SNAP Datasets: Stanford Large Network Dataset Collection," Jun. 2014. [Online]. Available: https://snap.stanford.edu/data/
R. Kumar, J. Novak, and A. Tomkins, "Structure and evolution of online social networks," in Proceedings of the 12th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, 2006, pp. 611–617.
A. Acquisti and R. Gross, "Predicting social security numbers from public data," Proceedings of the National Academy of Sciences, vol. 106, no. 27, pp. 10975–10980, 2009.
J. He, W. W. Chu, and Z. V. Chen, "Tagging systems: Privacy and security concerns," Journal of Web Semantics, vol. 9, no. 4, pp. 300–320, Dec. 2011.
L. Liu, C. Wang, and L. Zhang, "Privacy-preserving audience targeting in social networks," IEEE Transactions on Knowledge and Data Engineering, vol. 26, no. 12, pp. 2992–3005, Dec. 2014.
H. Liu, Y. Zhang, and X. Chen, "Blockchain-enabled privacy-preserving photo sharing in social networks," IEEE Transactions on Information Forensics and Security, vol. 15, pp. 2819–2829, 2020.
K. Lee, "Tagging and conflict management in social media: Privacy concerns," Journal of Social Media Studies, vol. 12, no. 3, pp. 233–247, Sep. 2018.
G. D. Abowd and E. D. Mynatt, "Charting past, present, and future research in ubiquitous computing," ACM Transactions on Computer-Human Interaction, vol. 7, no. 1, pp. 29–58, Mar. 2000.
S. L. Young and A. Quan-Haase, "Privacy protection strategies on Facebook: The Internet privacy paradox revisited," Information, Communication & Society, vol. 16, no. 4, pp. 479–500, Apr. 2013.
C. J. Hoofnagle, S. Urban, and S. Li, "Privacy and advertising mail preferences in the age of Big Data," IEEE Internet Computing, vol. 21, no. 1, pp. 48–55, Jan. 2017.
E. B. Korn and M. Lightstone, "Tagging and user consent mechanisms in online social platforms," International Journal of Privacy Studies, vol. 10, no. 2, pp. 104–122, Mar. 2019.